Privacy by Design: All You Need To Know
Privacy by Design is essential for building compliant technologies that respect user privacy. This article will go over what Privacy by Design is and how your business can implement it.

Overview
- What Is Privacy by Design?
- The Principles of Privacy by Design
- Why Privacy by Design Matters
- Why Privacy by Design Is So Hard
- How to Implement Privacy by Design Business Practices
What Is Privacy by Design?
Privacy by Design (PbD) is the approach of embedding privacy within products and services during the design and development process. It's based on the belief that legal frameworks alone cannot ensure privacy compliance. Rather, privacy must be an essential part of systems engineering.
The philosophy behind Privacy by Design was developed by Dr. Ann Cavoukian, Ph.D in response to growing privacy concerns from technological developments in the 1990s. In 2010, Privacy by Design was accepted as the international standard of data privacy compliance by the International Assembly of Privacy Commissioners and Data Protection Authorities.
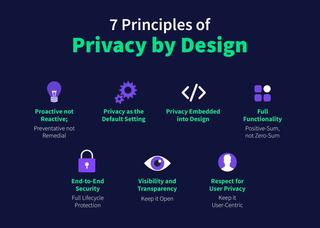
Privacy by Design includes seven foundational principles:
- Proactive not Reactive; Preventative not Remedial
- Privacy as the Default Setting
- Privacy Embedded into Design
- Full Functionality – Positive-Sum, not Zero-Sum
- End-to-End Security – Full Lifecycle Protection
- Visibility and Transparency – Keep it Open
- Respect for User Privacy – Keep it User-Centric
Let's examine these principles of privacy in more detail.
The Principles of Privacy by Design
Privacy by Design Principle #1: Proactive not Reactive
Privacy by Design is a proactive privacy approach to protect users' data. It empowers businesses to evaluate their product or service's privacy practices before releasing it to the public. That way, businesses can prevent invasive privacy risks for users without managing personal data processing at the same time.
More often than not, companies consider privacy as an afterthought, meaning it's addressed outside of the Software Development Lifecycle (SLDC). After companies start attracting customers and collecting their data, their only option is addressing privacy issues as they crop up. In other words, reactively.
These business practices are an inefficient and unscalable way of solving privacy. Without addressing the problem at its root, businesses will stay in this vicious cycle. As a result, they'll lose a lot of time and money catching up with privacy issues as they arise.
For example, privacy teams spend an average of 83 hours to manually fulfill one Data Subject Request, costing businesses $1,700. Using Ethyca's proactive approach to privacy, in the form of Privacy as Code, this same task can be accomplished in 17.2 seconds.
By anticipating privacy vulnerabilities, businesses can also proactively embed privacy policies into the tech stack to ensure data is used only according to stated purposes. This is especially helpful when new privacy regulations pass, and will save engineering and legal teams lots of pain and friction.
Privacy by Design Principle #2: Privacy as the Default Setting
This fundamental principle of Privacy by Design ensures that all user data is automatically protected. Users would not need to manage their privacy settings or be wary of how businesses use their data. Instead, they can rest assured that their data is protected by default. It's not up to the user to protect their privacy; it's the businesses' responsibility.
Practicing this privacy approach is a way for businesses to enable users' data privacy from the earliest stages. Instead of retroactively going into the data structures to fix privacy issues or fulfill user requests, privacy would be built directly into the system. In other words, it's protection by default.
Here are ways to practice privacy by default:
- Purpose specification: clearly define the purpose of why your business is collecting specific user information. These reasons must be clear, relevant, and not excessive.
- Data minimization: collect the bare minimum of users' personally identifiable information (PII). Ensure that data collected is being used only for stated purposes, and not filtering into other business systems or processing activities.
- Use, retention, and disclosure limitation: Limit the use, retention, and disclosure of users' PII to what they have consented to. Whatever data is collected should be kept only to fulfill its purpose, and then deleted securely.
These practices will help ensure that respect for privacy is the default state of your system. Doing this work upfront also helps protect an organization from damaging privacy breaches in the future.
Privacy by Design Principle #3: Privacy Embedded into Design
The previous Privacy by Design principle focuses on protection by default. The next one emphasizes protection by design.
Protecting user data by default doesn't just magically happen. Businesses need to consciously make the effort to embed privacy into the design and architecture of their systems. This will not only help the businesses fulfill their legal obligations, it will also help them gain user trust.
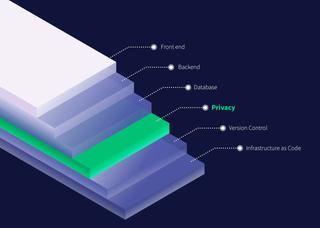
Again, privacy should not be considered an add-on after the business has started collecting user data. Rather, privacy should be baked into the system's technology. In practice, this could look like a privacy metadata layer that is easily governable by system owners. Organizations can use this privacy layer to ensure that they have full context and control over the data they posses.
Privacy by Design Principle #4: Full Functionality
Privacy by Design does not sacrifice other forms of functionality for privacy. In other words, it's not a zero-sum bargain. Rather, privacy is a "win-win" situation.
According to this principle of Privacy by Design, It's a false dichotomy to pit privacy against user experience. Users should not have to compromise their privacy in order to fully enjoy the offerings of a product or system.
A good example of this principle can be found in California's CCPA. Under CCPA, a data processor cannot withhold parts of their service if the user does not opt into data collection. In other words, a product can’t withhold functionality in exchange for privacy concessions.
Privacy by Design Principle #5: End-to-End Security
As an important part of designing privacy into products or services, user data should remain secure throughout its entire lifecycle. Ensuring strong security measures in business practices will protect user data from the second it's collected until it's deleted off the systems.
Although data security and data privacy are different, it's not possible to have data privacy without data security. This includes secure data deletion, strong access controls, and strong encryption. Without end-to-end security, there is no Privacy by Design.
Applying strong security measures allows businesses to collect, process, and store user data without exposing users to vulnerabilities.
Privacy by Design Principle #6: Visibility and Transparency
Privacy by Design aims to hold businesses accountable for their privacy practices. Under this data protection principle, businesses must prove they are doing what they say they're doing with user data.
In other words, a business' data practices should be demonstrable. They should undergo frequent independent reviews of their privacy practices, such as external audits, and conduct privacy impact and risk assessments.
Doing so will help users and other stakeholders verify whether or not their data is being managed respectfully. These efforts will lead to trust between consumers and businesses.
Privacy by Design Principle #7: Respect for User Privacy
At the heart of Privacy by Design is an inherent respect for user privacy. Keeping individuals' data privacy top of mind is a way for businesses to ensure that they are respecting users' privacy rights.
To make sure it's happening, system owners can ask themselves: "am I handling user data the way I'd want my own data to be treated? Are we managing user data in a way that intentionally respects their privacy rights?"
Answering these questions will guide your organizations' data privacy decisions. It will also help businesses establish strong security measures, such as protection by default and protection by design.
In short, Businesses must keep their technologies user-centric. This commitment to user privacy will also help them build a trusting relationship with consumers.
Why Privacy by Design Matters
Advancements in technology have led to an astronomical rise in data collection. More data is collected than ever before, and its value has never been greater. In this context, the principles of Privacy by Design matter more than ever. Businesses' commitment to user privacy will enable consumers the freedoms they need to live in the modern world. Therefore, privacy must be a priority for businesses that can engineer it in the products and services they use. It's why the authors of the General Data Protection Regulation (GDPR), Europe’s flagship privacy law, chose to enshrine Privacy by Design in its text.
There's no magic bullet for building respectful systems, but getting familiar with the principles of Privacy by Design is one of the best ways to start. Embedding privacy policies into your product or service's codebase will help you maintain compliance, avoid fines, and earn customers' trust. Engineering and legal teams can also avoid playing catchup with newly collected PII. Instead, engineers will be able to dedicate more time and effort shipping code, and legal teams will enjoy maintaining compliance.
Why Privacy by Design Is So Hard
In tandem with technological advancements, activities like data collection, storage, and deletion have gotten more complex. The days of record-keeping books in filing cabinets are long gone. Now, it's common for businesses to have unorganized data flowing across multiple different databases and systems.
Few could have predicted the ways that data collection would transform. Hence, current data structures cannot account for the scope and volume of data flowing throughout organizations. Only recently have consumers been more outspoken, urging businesses to treat their data more responsibly. The culture has changed and new data privacy regulations have passed. However, laws change faster than businesses, and it's now up to them to catch up on their data privacy practices.
Privacy must be designed purposefully in business systems. It is not something that can simply be tagged onto a product or business; it is a methodical process that takes years to build, where the pay-off will be seen in the long term.
The vast majority of today’s data infrastructure was not designed with privacy in mind. As a result, the status quo is retroactive, box-checking privacy. It can seem like an uphill fight to implement Privacy by Design, especially for companies that have already gone to market. But Privacy by Design is possible. Teams just need technical tools fit for the task. That’s why we've created the Fides platform – to do just that.
How to Implement Privacy by Design Business Practices
If you're just starting to implement Privacy by Design, you can organize your approach following the Privacy Maturity Pyramid.
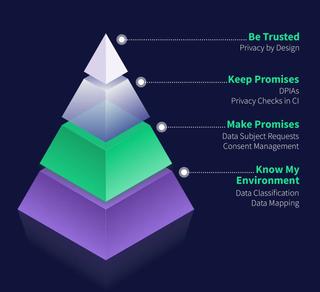
A business will sequentially tackle a series of privacy considerations as it grows in scale and data maturity. With a post-hoc approach to privacy, these considerations grow in complexity over time: the problems discovered tomorrow won't be solved by the solutions found today.
Even lower-order privacy challenges that can, in theory, be supported by post-hoc approaches quickly become laborious and error-prone at scale. Embedding privacy into systems design can allow these lower-order goals to be met even as businesses rapidly grow their technical infrastructure.
Privacy by Design Is A Proactive Privacy Approach to Business Practices
It's important to note that Privacy by Design doesn't just make the higher-order privacy needs feasible; they also simplify the processes to achieve lower-order privacy needs. A proactive approach, such as one modeled on the Privacy by Design framework, is necessary to meet privacy requirements at scale across evolving regulations and complex technical infrastructure.
Our team of data privacy devotees would love to show you how Ethyca helps engineers deploy CCPA, GDPR, and LGPD privacy compliance deep into business systems. Let’s chat!
Speak with Us






