Privacy Requests: Identifying & Debugging Issues
Introduction
In this tutorial, you'll learn how to review the event logs for a privacy request and identify issues that may require debugging.
Prerequisites
For this tutorial, you'll need:
- A Fides Cloud or Fides Enterprise account
- The role of either
Owner,View & ApproverorApproverto manage privacy requests. - At least one system integration configured for privacy requests. Read how to configure an integration.
- A privacy center to receive and process privacy requests. Read how to configure a privacy center.
Identifying Privacy Request Issues
From time-to-time, privacy requests can fail to process completely. This is often due to the sheer number of systems connected in a privacy process and how they depend on each other to complete successfully. A common reason for a privacy request to fail is expired credentials to a system, however, there can be a variety of other reasons. Identifying the cause as quickly as possible to remediate it is key.
Fides provides a detailed events and activities log for this very reason. Let's take a walk through of the feature now.
Viewing Request Logs
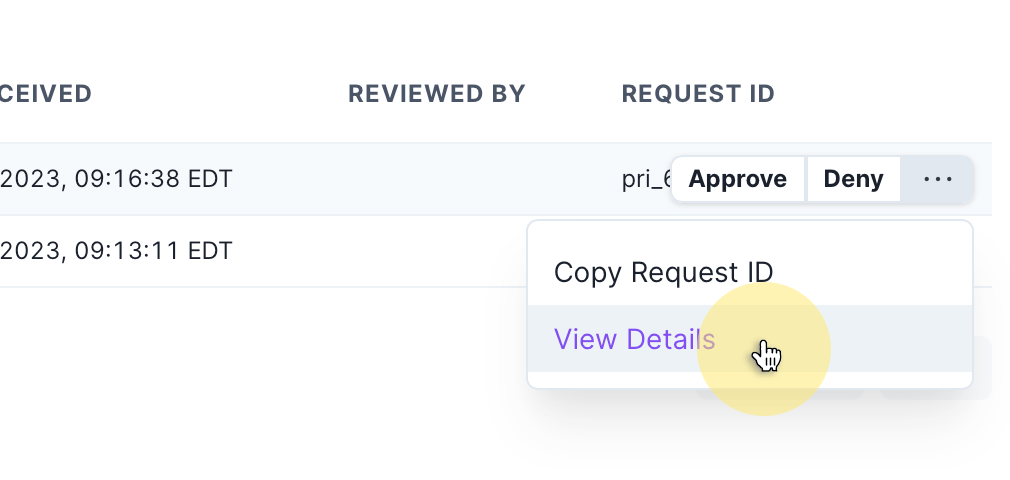
To view the event logs for a given request, click the kebab menu ... and select View Details as follows:
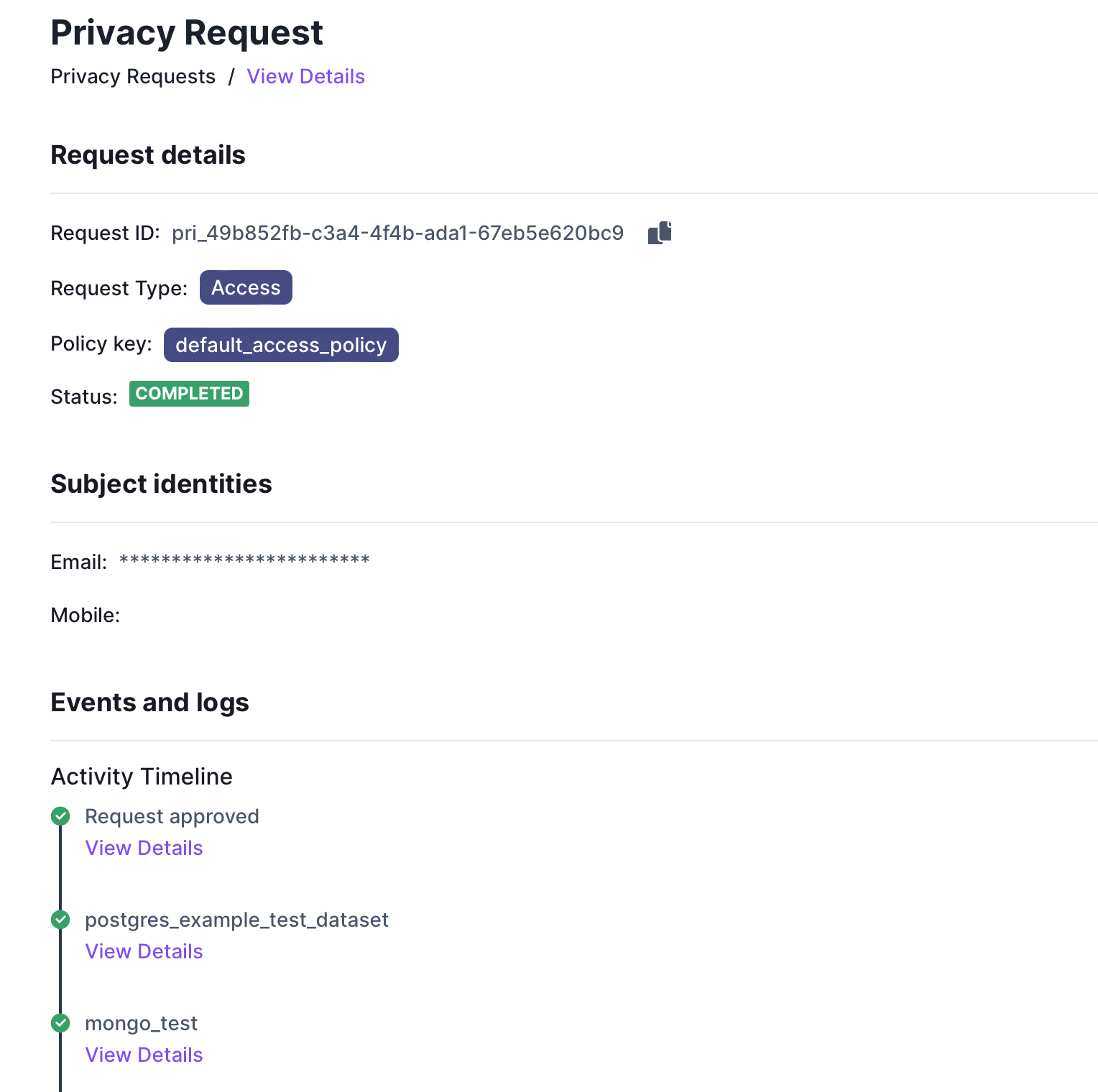
If the privacy request has already been processed, the event logs will show a list of the processed systems under Events and Logs as shown below:
To view the the details of a specific system's privacy request processing, click on "View Details" and then "View log" to show the detailed processing log for the system:
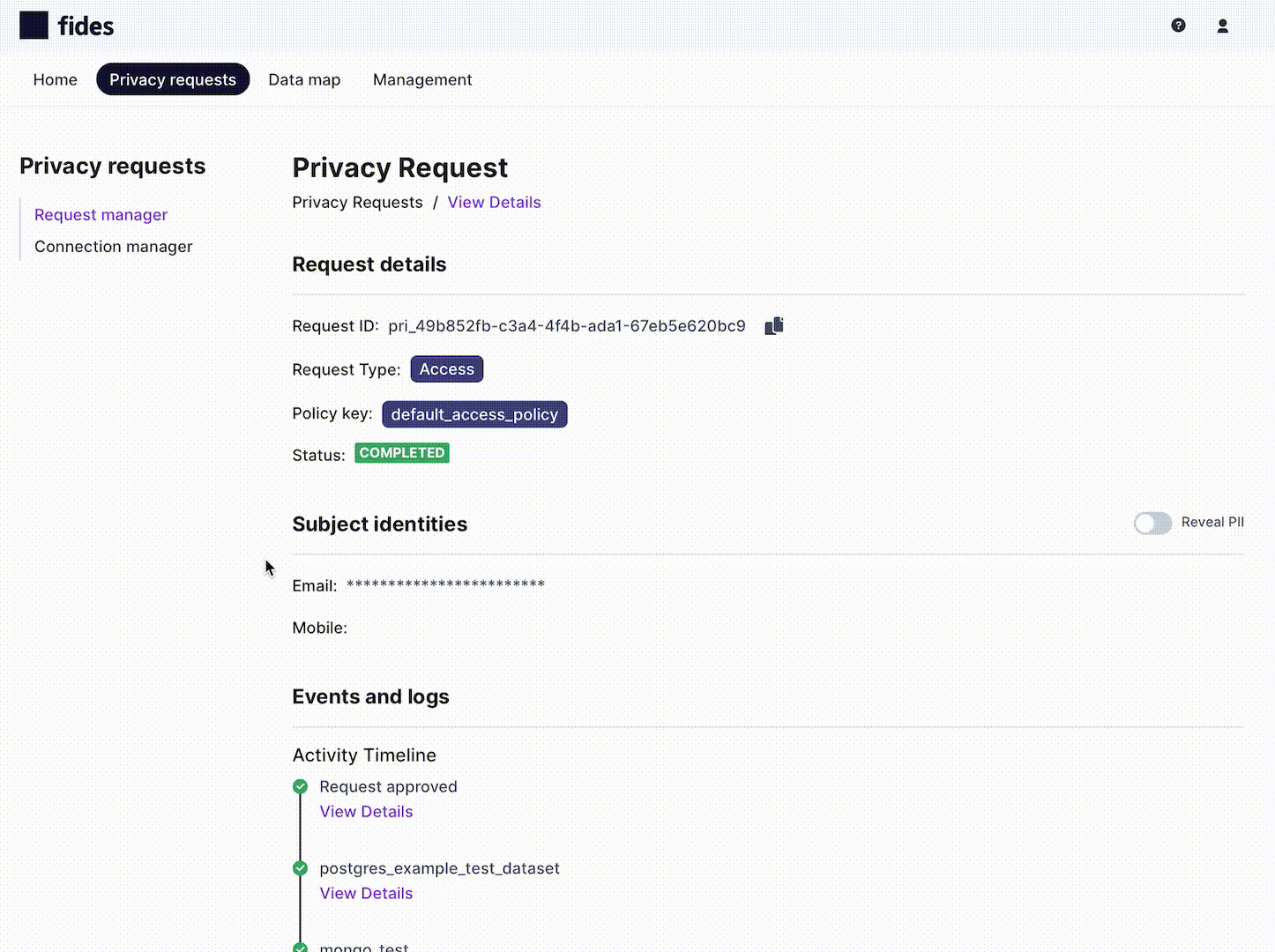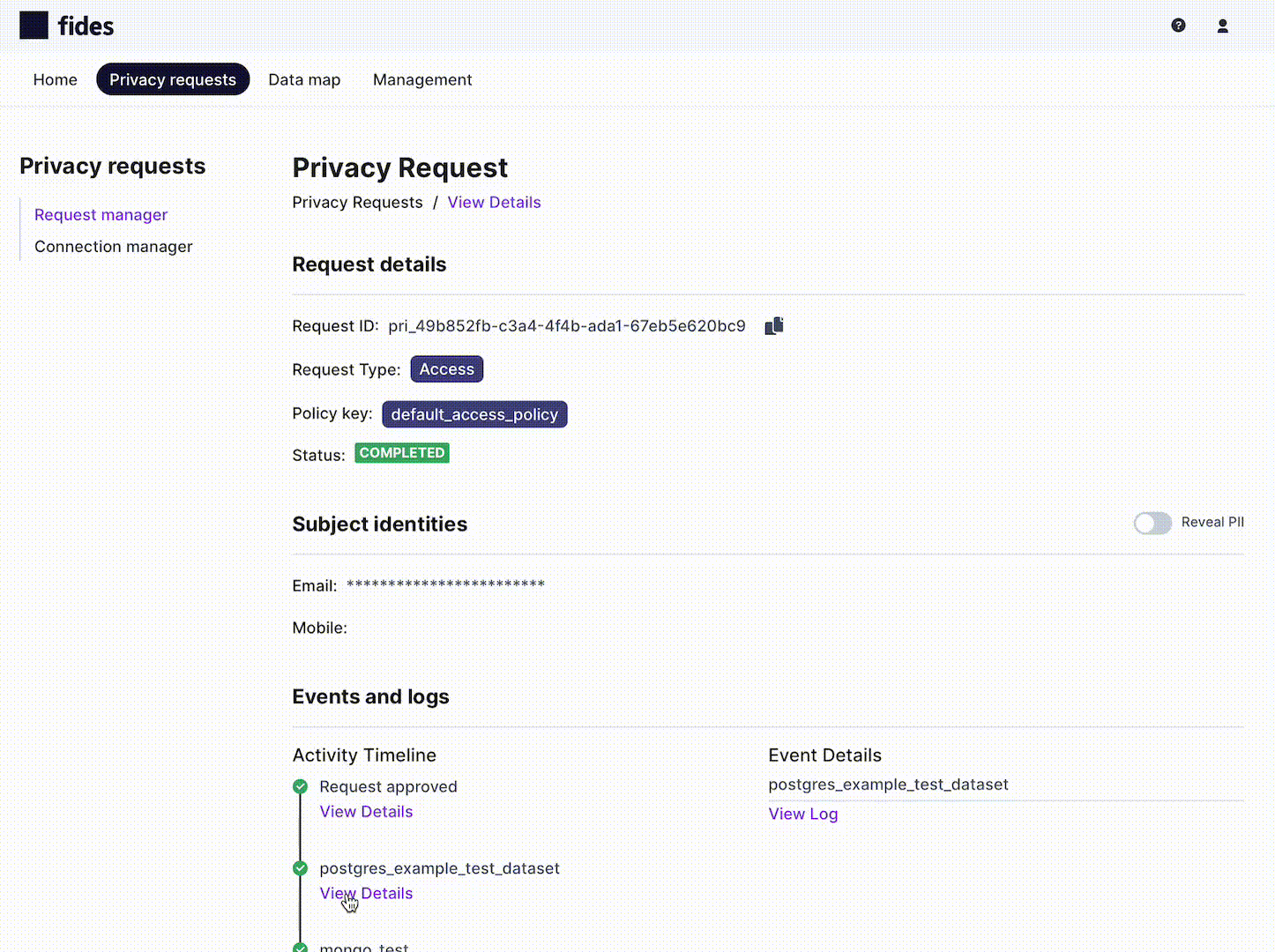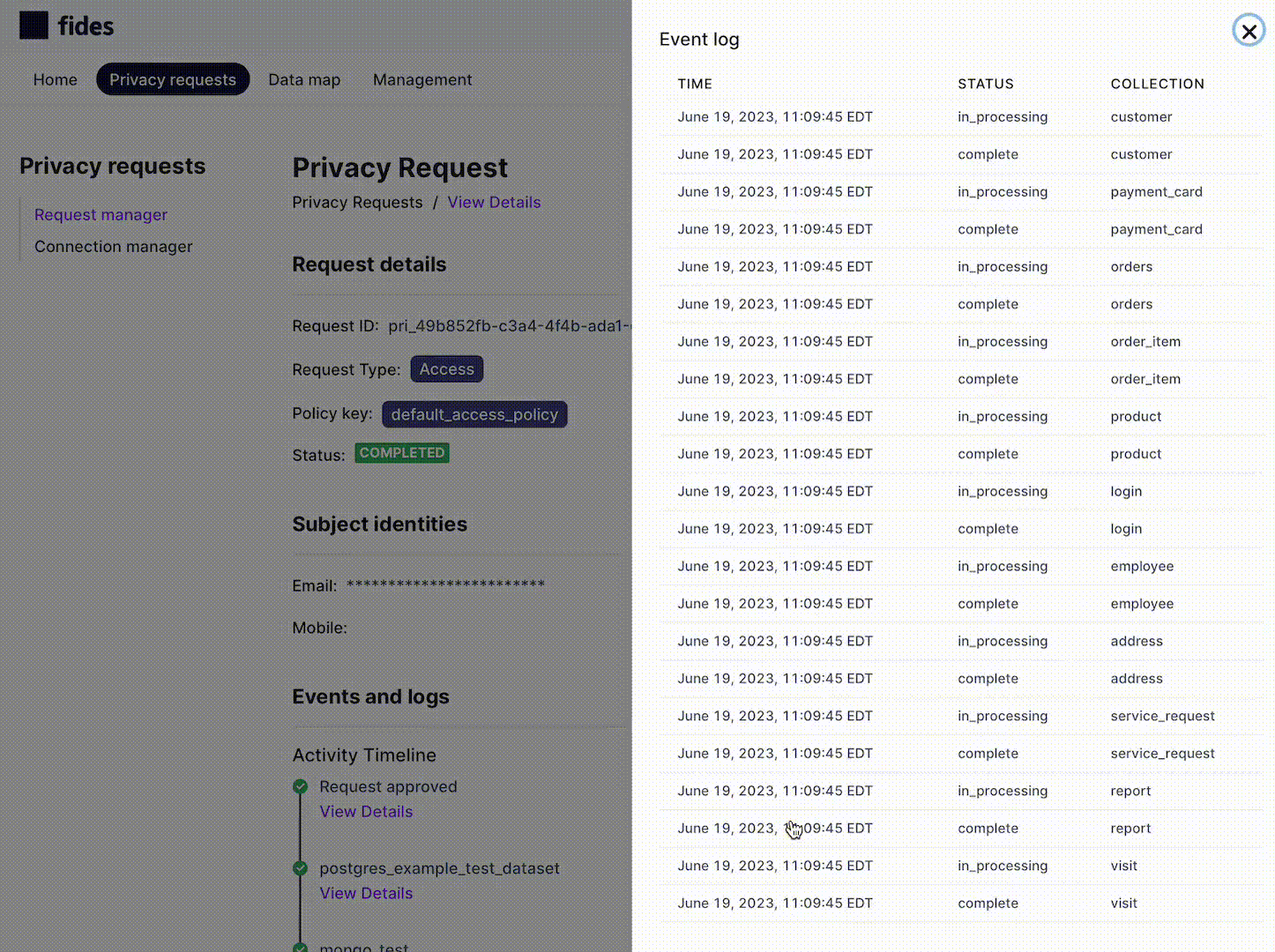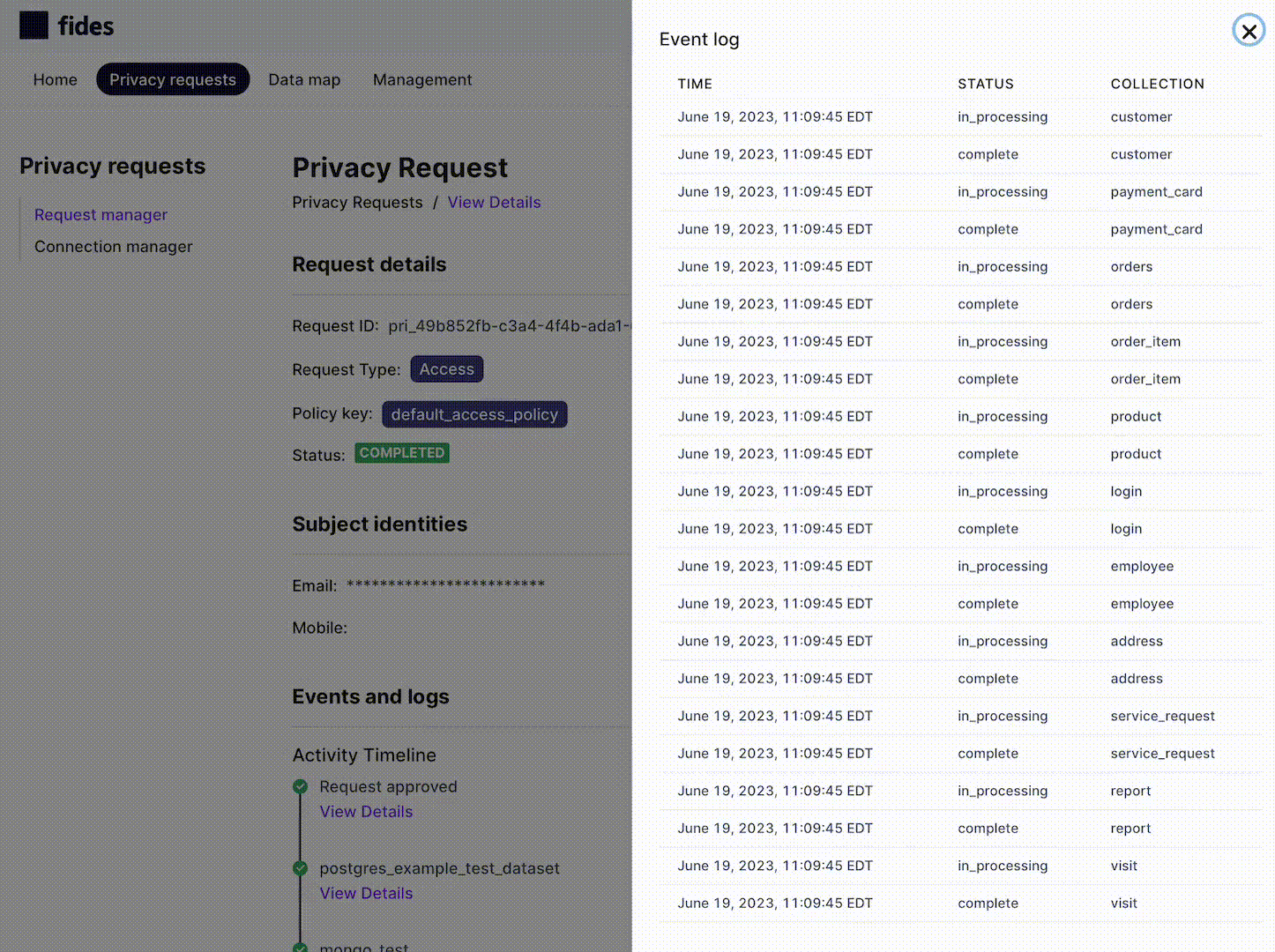
This detailed view of events shows exactly what action has been performed for each system and the available collections, so you can identify precisely where an issue occurs with a privacy request for debugging.