Privacy Requests: Workflow
4minFidesPrivacy Requests
This tutorial requires Fides Cloud or Fides Enterprise. For more information, talk to our solutions team. (opens in a new tab)
Introduction
In this tutorial, you'll learn about the flow of privacy requests from start to finish. You'll cover the process for a subject to submit their request on the privacy center, through to reviewing, rejecting and approving requests in Fides Control. By the end of this tutorial, you'll understand how privacy requests are submitted and processed in Fides.
Prerequisites
For this tutorial, you'll need:
- A Fides Cloud or Fides Enterprise account
- The role of either
Owner,View & ApproverorApproverto manage privacy requests. - At least one system integration configured for privacy requests. Read how to configure an integration.
- A privacy center to receive and process privacy requests. Read how to configure a privacy center.
Privacy Request Flows
Before processing a privacy request, we'll look briefly at the steps and flow of a typical request:
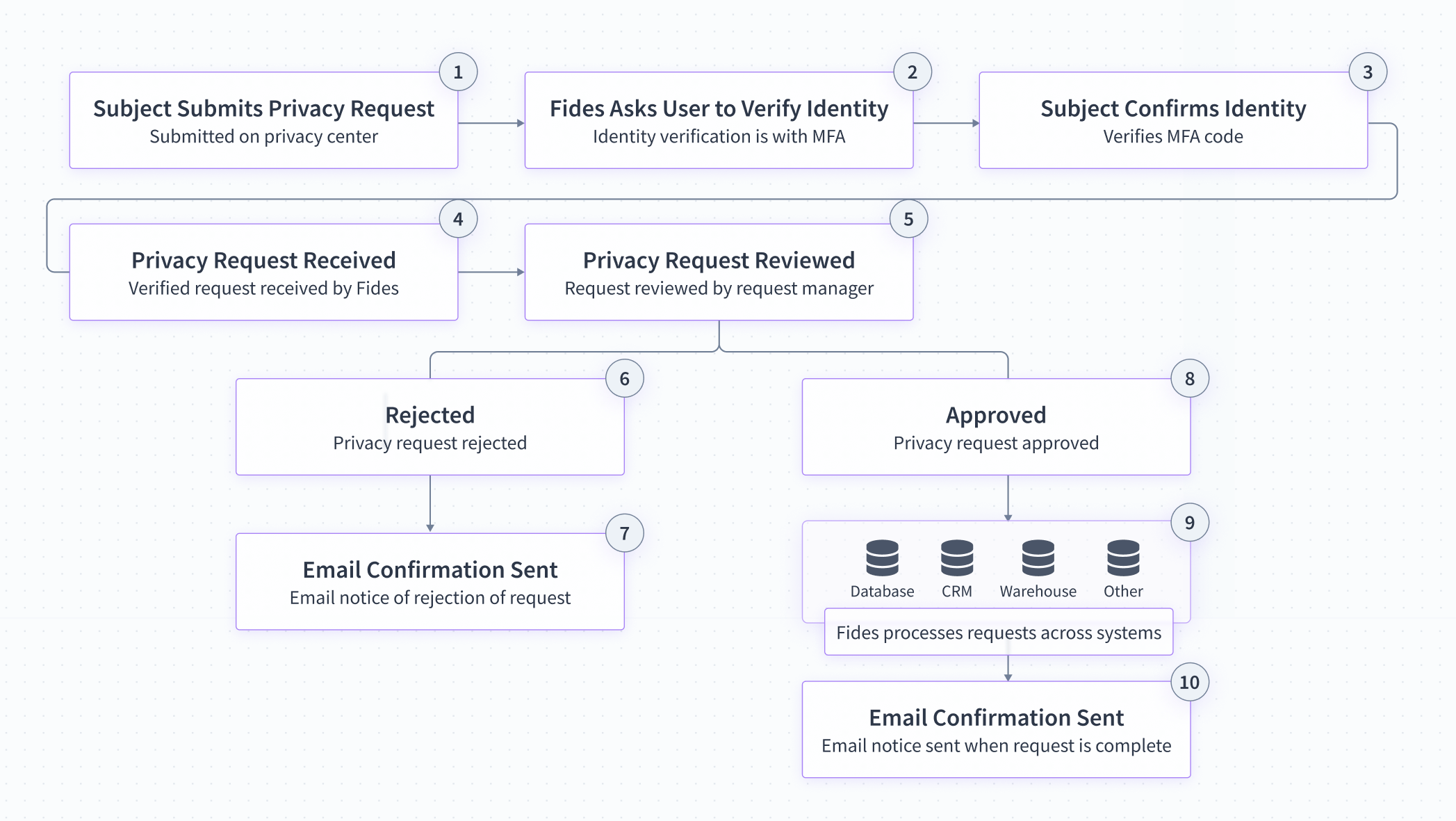
- Subject Submits Privacy Request: The user (subject) submits a privacy request through the privacy center.
- Identity Verification: Fides sends a code to the user's email address or phone number to verify their identity.
- Subject Confirms Identity: The subject confirms their identity using the code provided.
- Privacy Request Received: The privacy request is recorded on Fides with the subject's identity verification.
- Privacy Request Reviewed: Privacy requests are reviewed by an appointed request manager.
- Rejected: When a privacy request is rejected, Fides records the reason for rejecting the request.
- Email Confirmation Sent: An email confirming that the request has been rejected is sent to the subject.
- Approved: When a privacy request is approved, Fides commences processing the request.
- Fides Processes Request: Fides processes the privacy request programmatically across all integrated systems.
- Email Confirmation Sent: An email confirming the request has been completed is sent to the subject.
Next, we'll look at each step in the flow in detail.