Privacy Requests: Submitting Requests
Introduction
In this tutorial, you'll learn how your users can submit privacy requests. You'll cover the process for a subject to submit their request on the privacy center, verify their identity, and then receive the request.
Prerequisites
For this tutorial, you'll need:
- A Fides Cloud or Fides Enterprise account
- The role of either
Owner,View & ApproverorApproverto manage privacy requests. - At least one system integration configured for privacy requests. Read how to configure an integration.
- A privacy center to receive and process privacy requests. Read how to configure a privacy center.
Submitting a Privacy Request
Fides provides a pre-built privacy center for your subjects to submit privacy requests. Read about configuring your privacy center here.
Typically, your privacy center is configured to be available on a subdomain of your brand website, such as: https://privacy.your-brand.com.
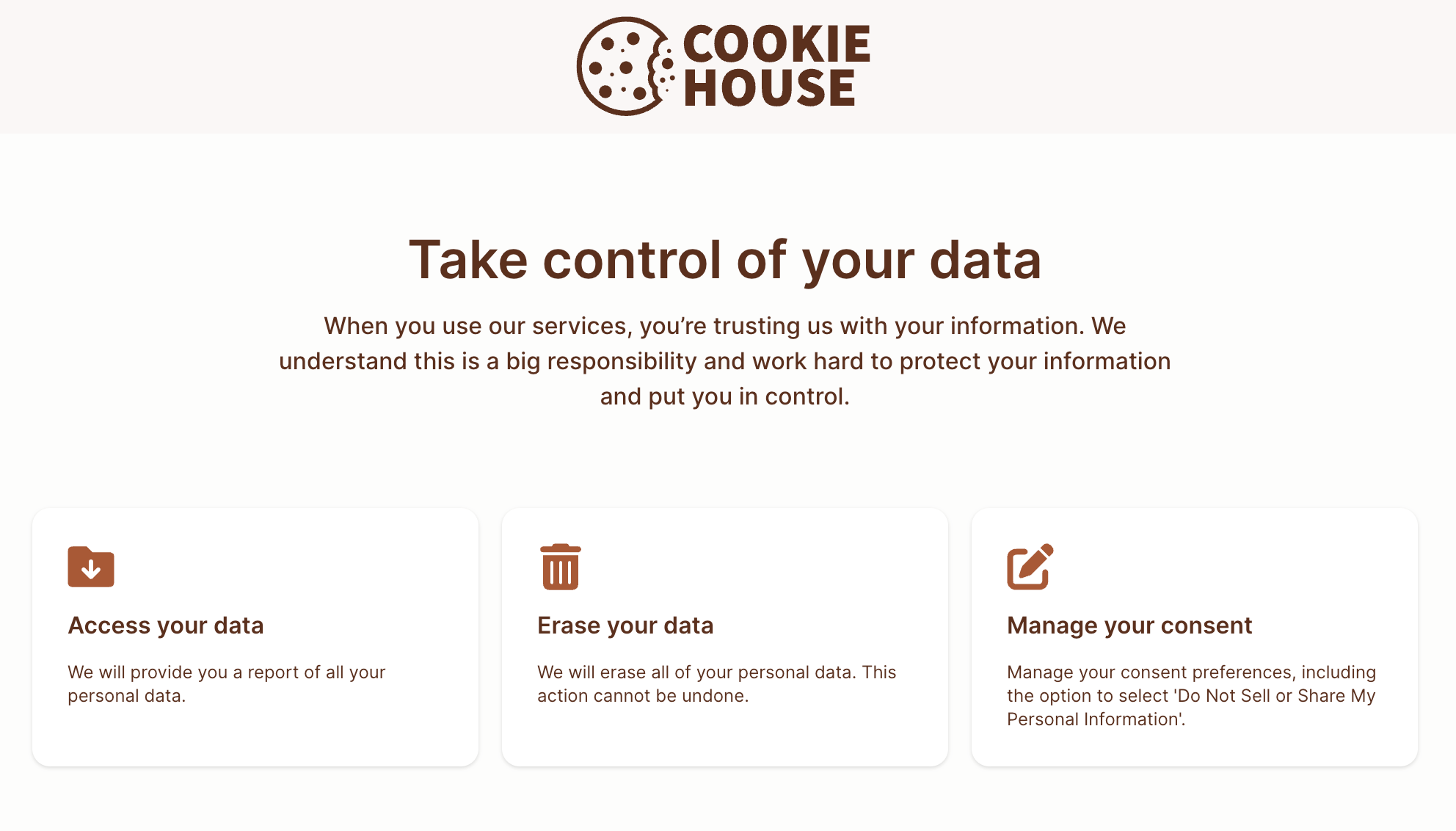
The example above shows a sample privacy center for the "Cookie House" sample project.
To submit a privacy request, the subject must provide an identifier, such as their email address or phone number, as shown in the example below:
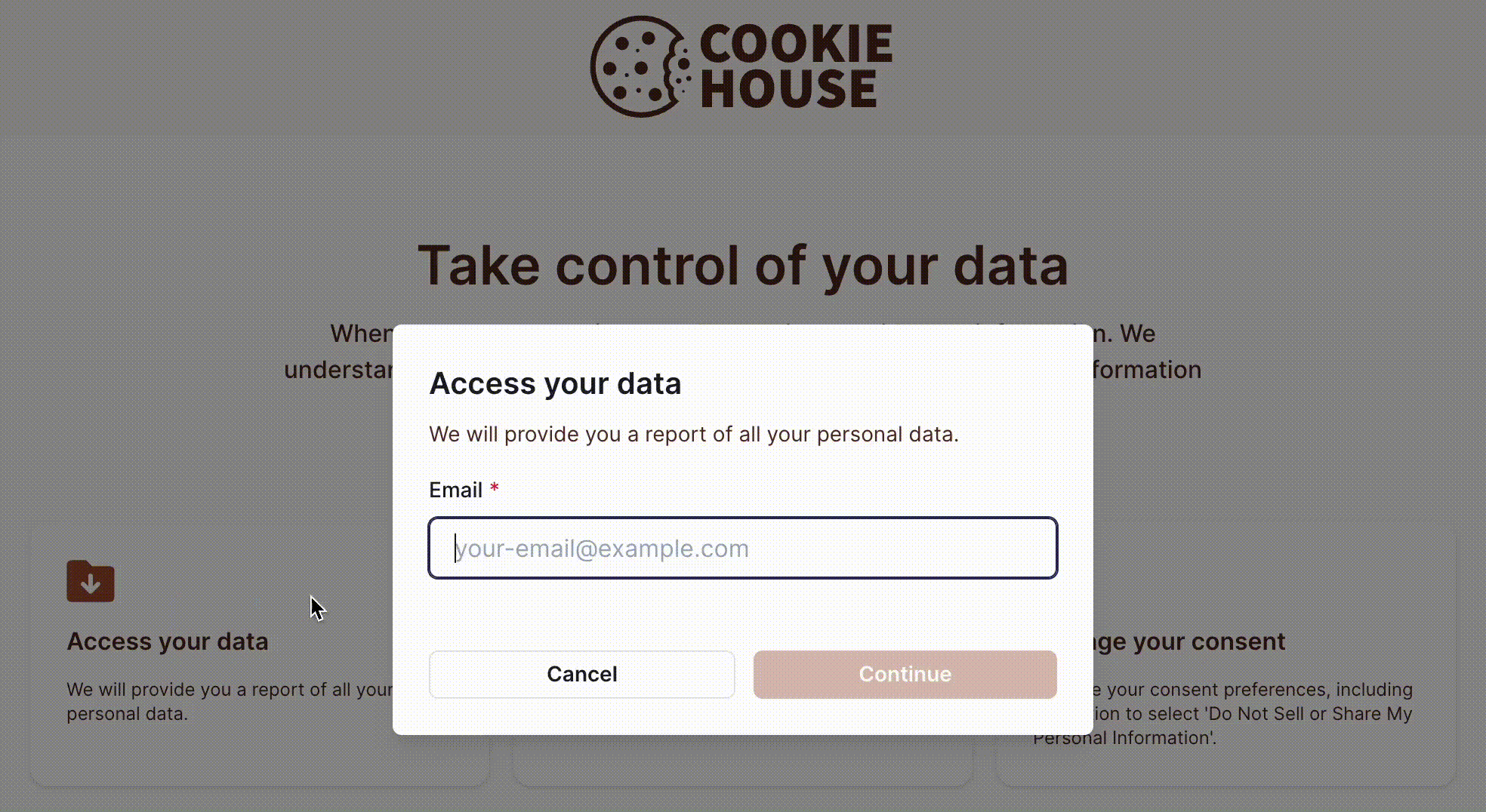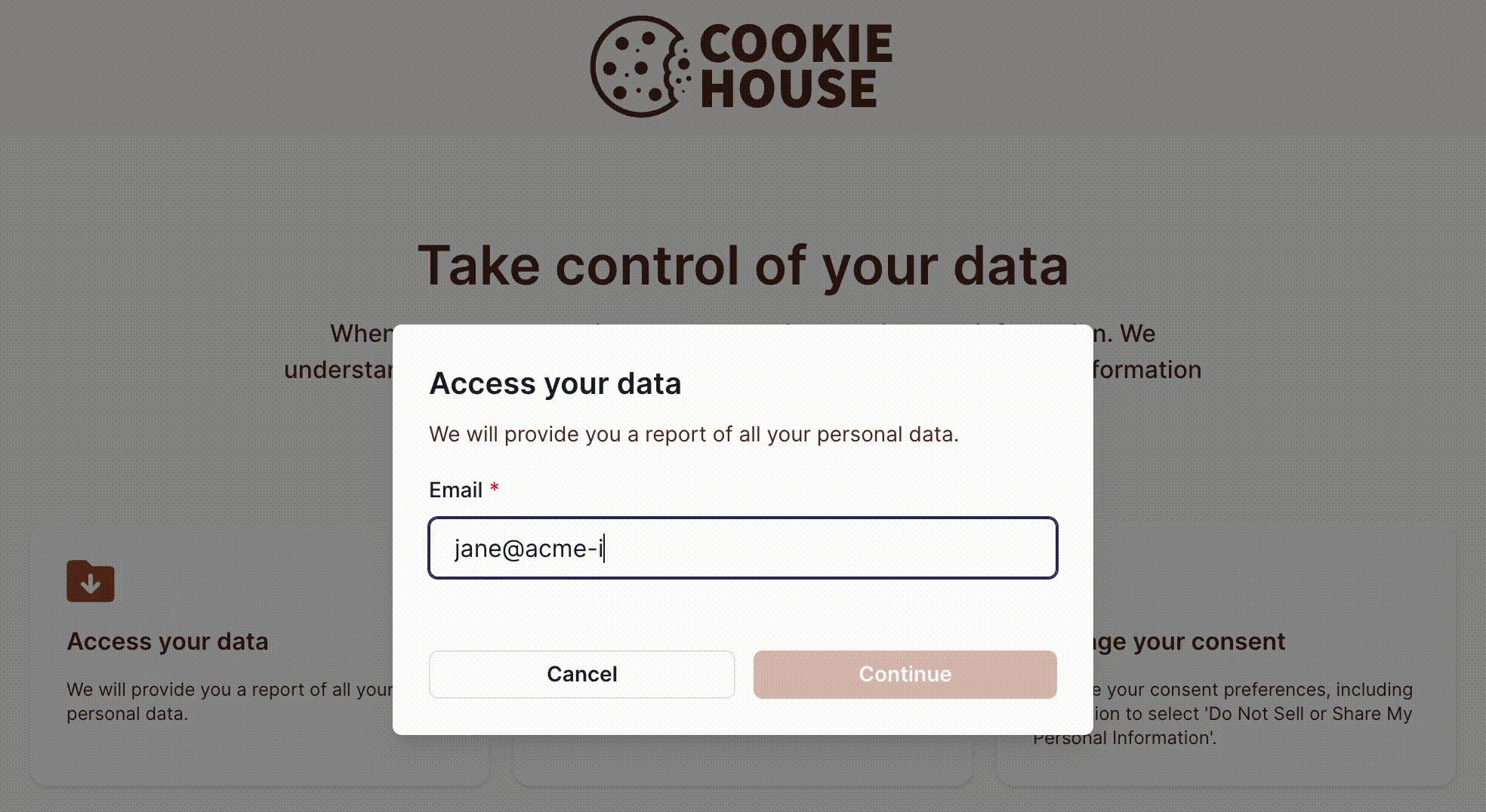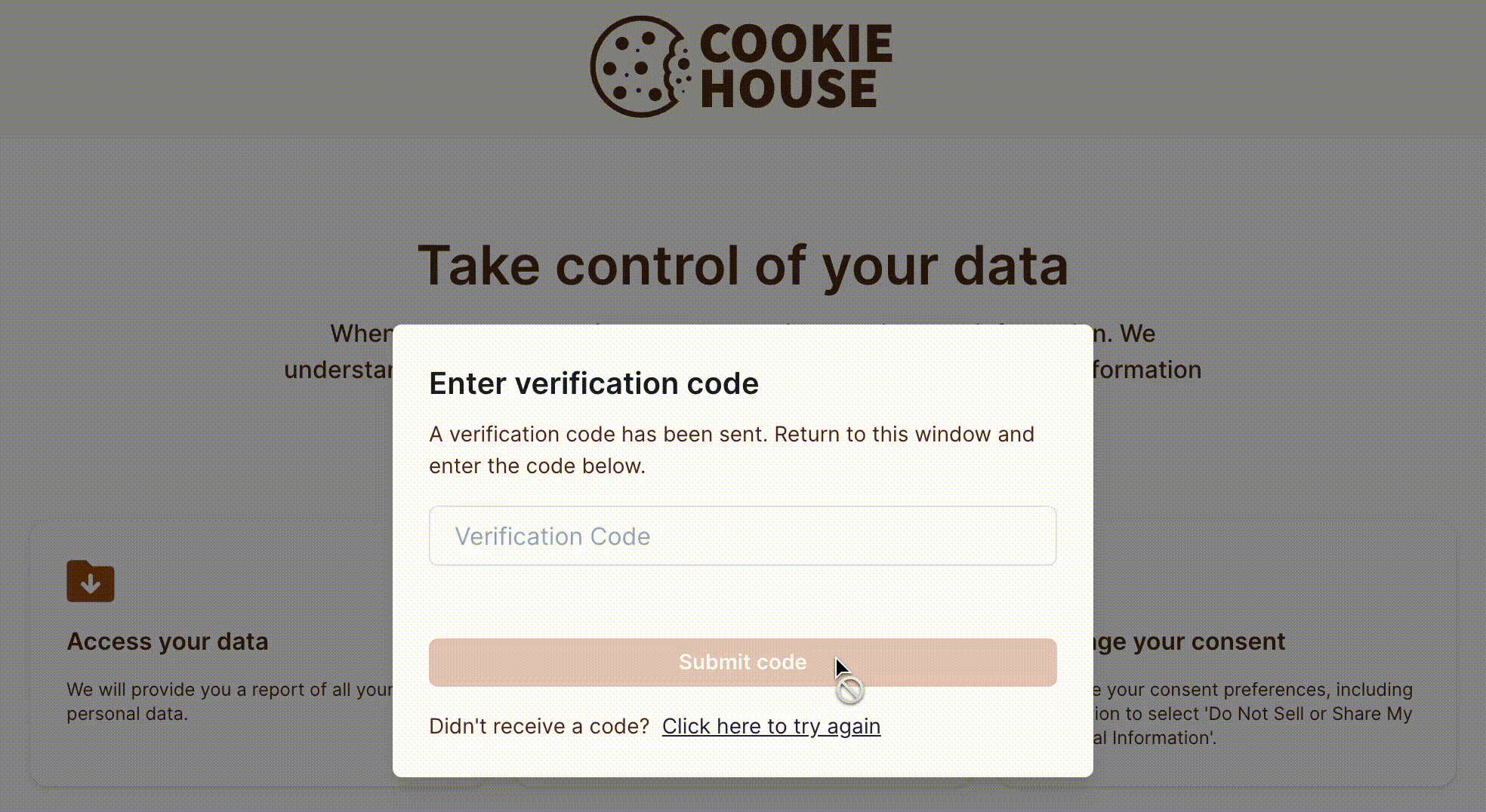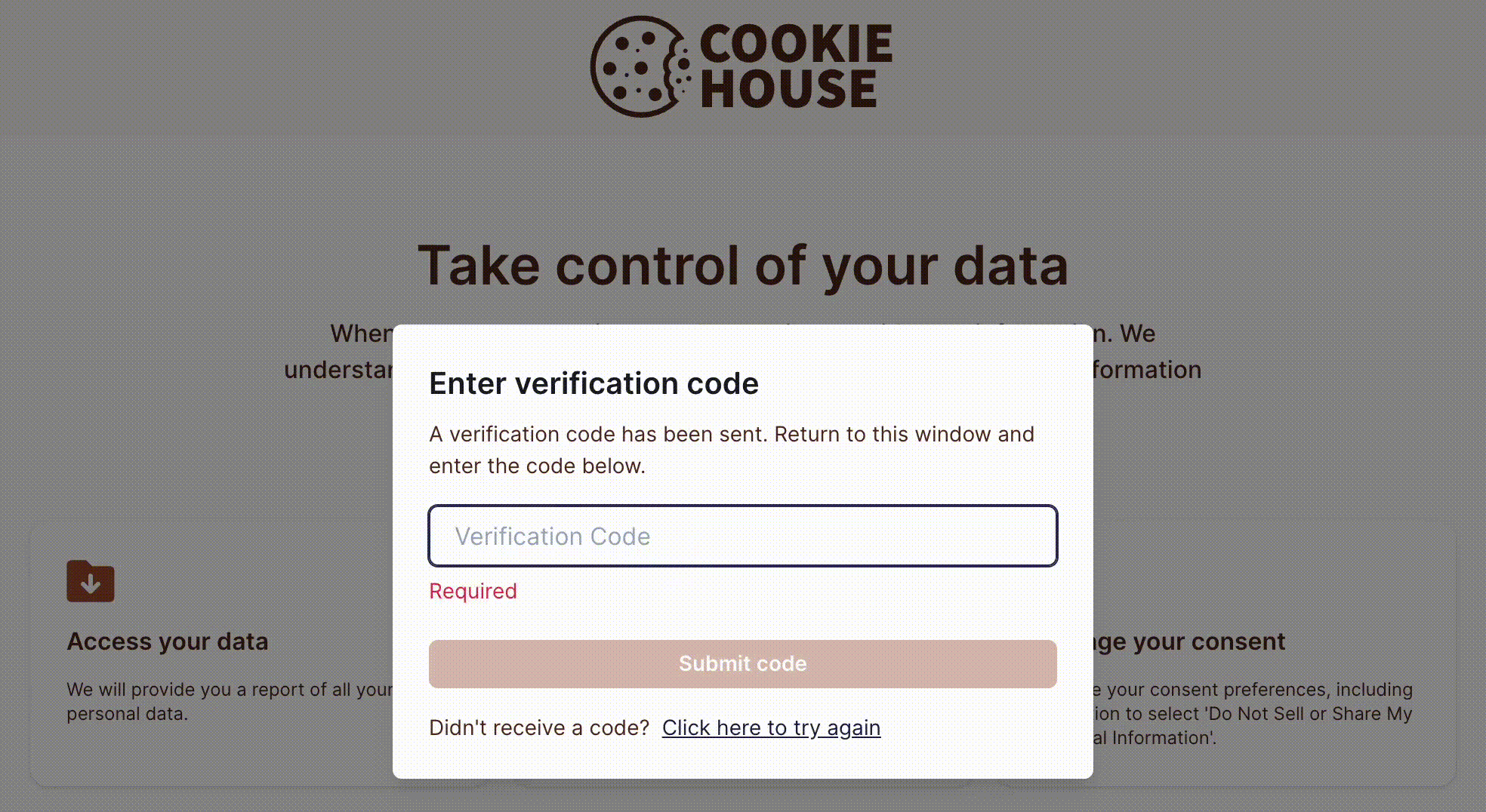
Subject Identity Verification
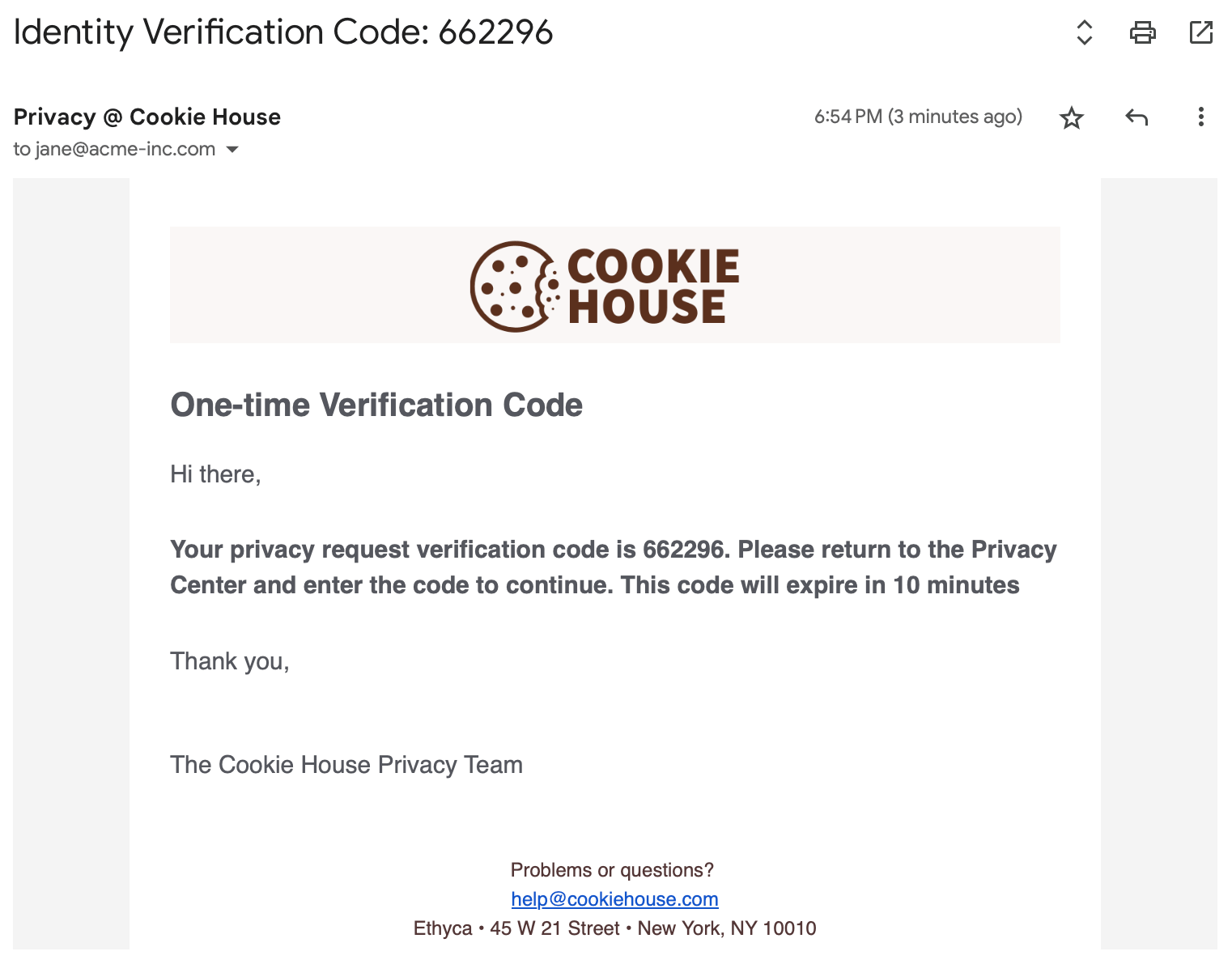
If subject identity verification is enabled, the subject will receive a code to their email address or phone number to confirm their identity when they submit a privacy request.
Below is an example of the email received for the "Cookie House" sample project.
The subject provides the code when prompted on the privacy center to verify their identity as shown below:
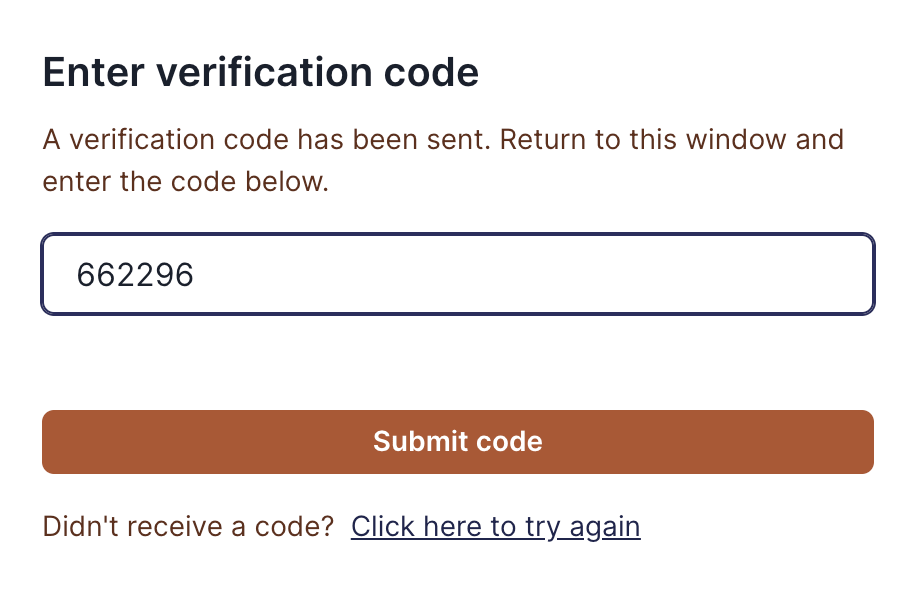
You can configure whether you would like to have identity verification on your privacy center. Read about configuring identity verification here.
Next, we'll look at how to review and approve privacy requests.