Receiving privacy requests
Data subjects have several rights when it comes to the protection and processing of their personal data. These rights may vary depending on the specific data protection regulations applicable in a given jurisdiction, such as the European Union's General Data Protection Regulation (GDPR). But, here are some commonly recognized rights:
- Right to Access: The user has the right to access the personal data that was collected and processed about them, and understand what purposes it was used for.
- Right to Erasure: The user has the right to have all personal data deleted across the entire organization.
- Right to Rectification: The user has the right to correct personal information that the user believes to be incorrect about them.
- Right to Portability: The user has the right to obtain a machine-readable copy of their personal data such that it might be imported to another system.
To exercise these rights, data subjects typically submit a privacy request.
Ease of access
Many privacy regulations require businesses to provide a minimum of two easy-to-find methods for making privacy requests. The most common methods to receive privacy requests include:
- Form: A publicly available form on your website or application, where a user may submit their privacy request.
- Email: A publicly available email address, where a user may submit their privacy request.
- Phone: A publicly available phone number, where a user may contact you to submit their privacy request.
Subject identity verification
When a privacy request is received, your organization is responsible for confirming the identity of the subject to ensure that you do not incorrectly disclose data.
To verify an identity, you may only request information that you already have concerning a data subject. For example, you can't request a copy of a subject's drivers license if you don't already have this information.
Ethyca recommends enabling identity verification for data subject requests. Fides verifies identities by sending a one-time passcode (OTP) to the data subject to verify that the request comes from the owner of the identity (email or phone number). To learn more, please see our guide for configuring subject identity verification.
Authorized agents
In some locations, a data subject may appoint a third party, typically known as an authorized agent, to submit privacy requests on their behalf.
If you receive a privacy request from an agent, you must honor it provided you are satisfied that the authorized agent has been appointed by the subject.
The Privacy Center
Fides offers an out-of-the-box Privacy Center to make it easy to receive privacy requests.
Typically, your Privacy Center is configured to be available on a subdomain of your brand website, such as: https://privacy.your-brand.com.
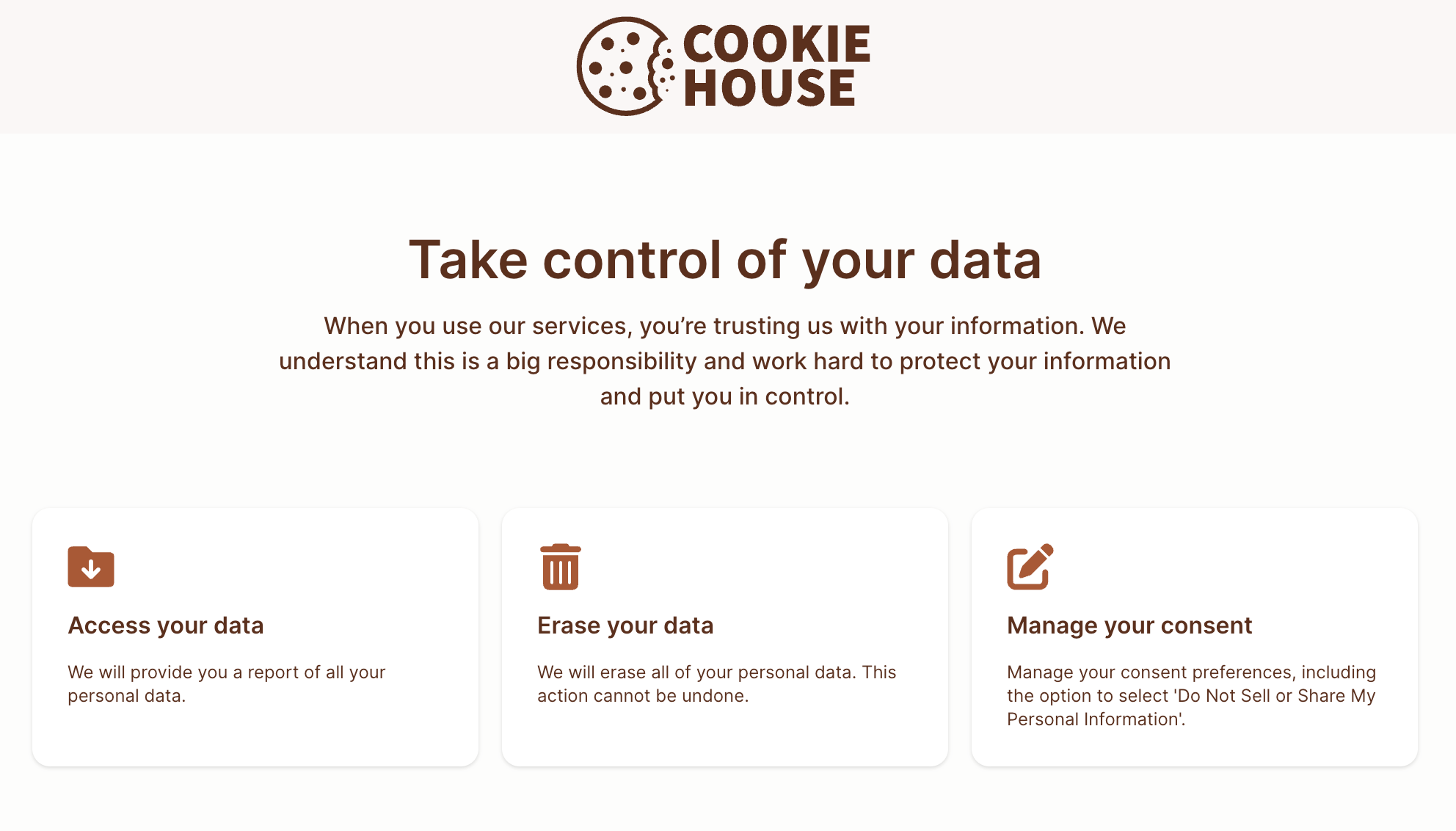
The example above shows a sample privacy center for the "Cookie House" sample project.
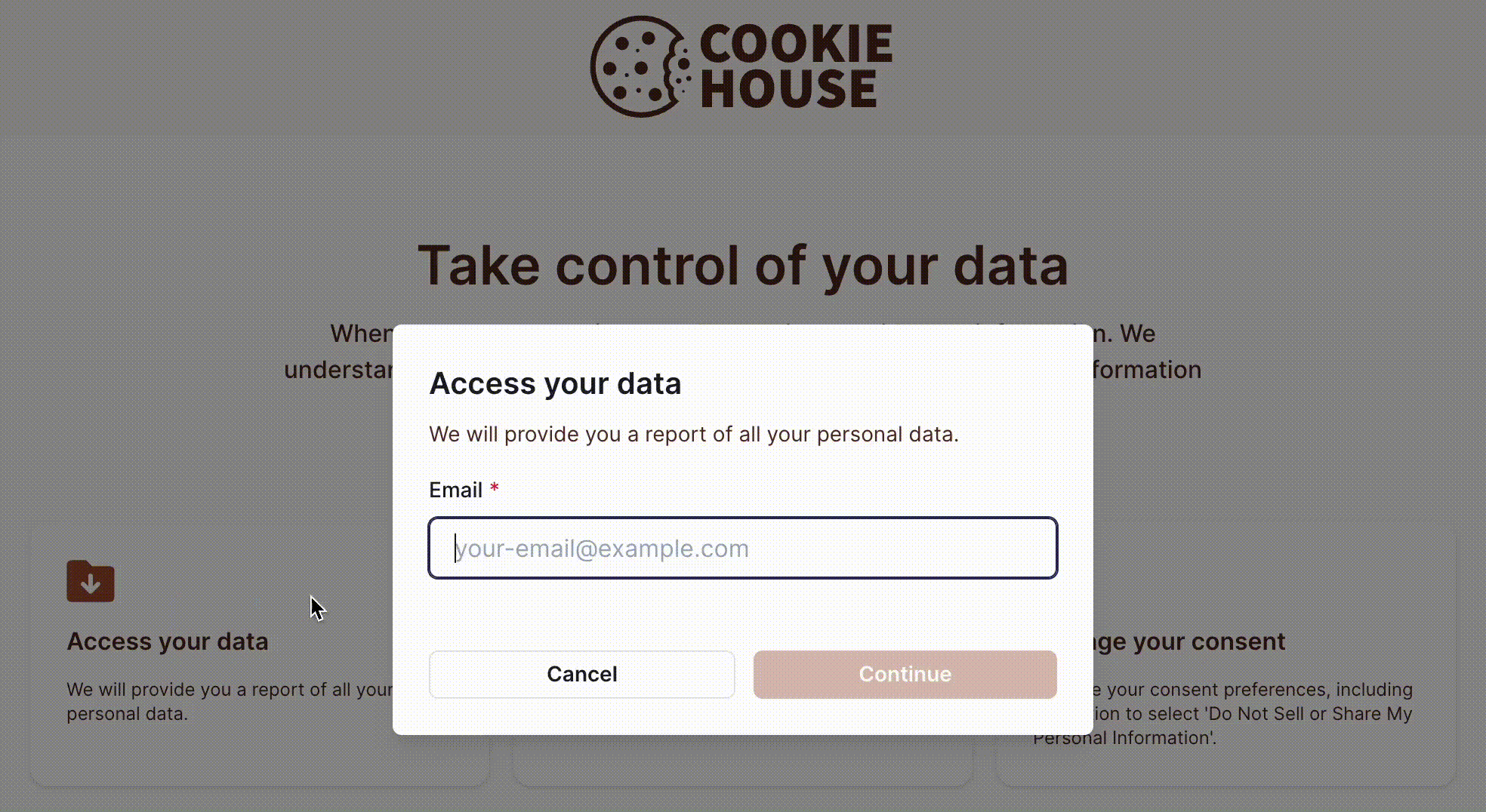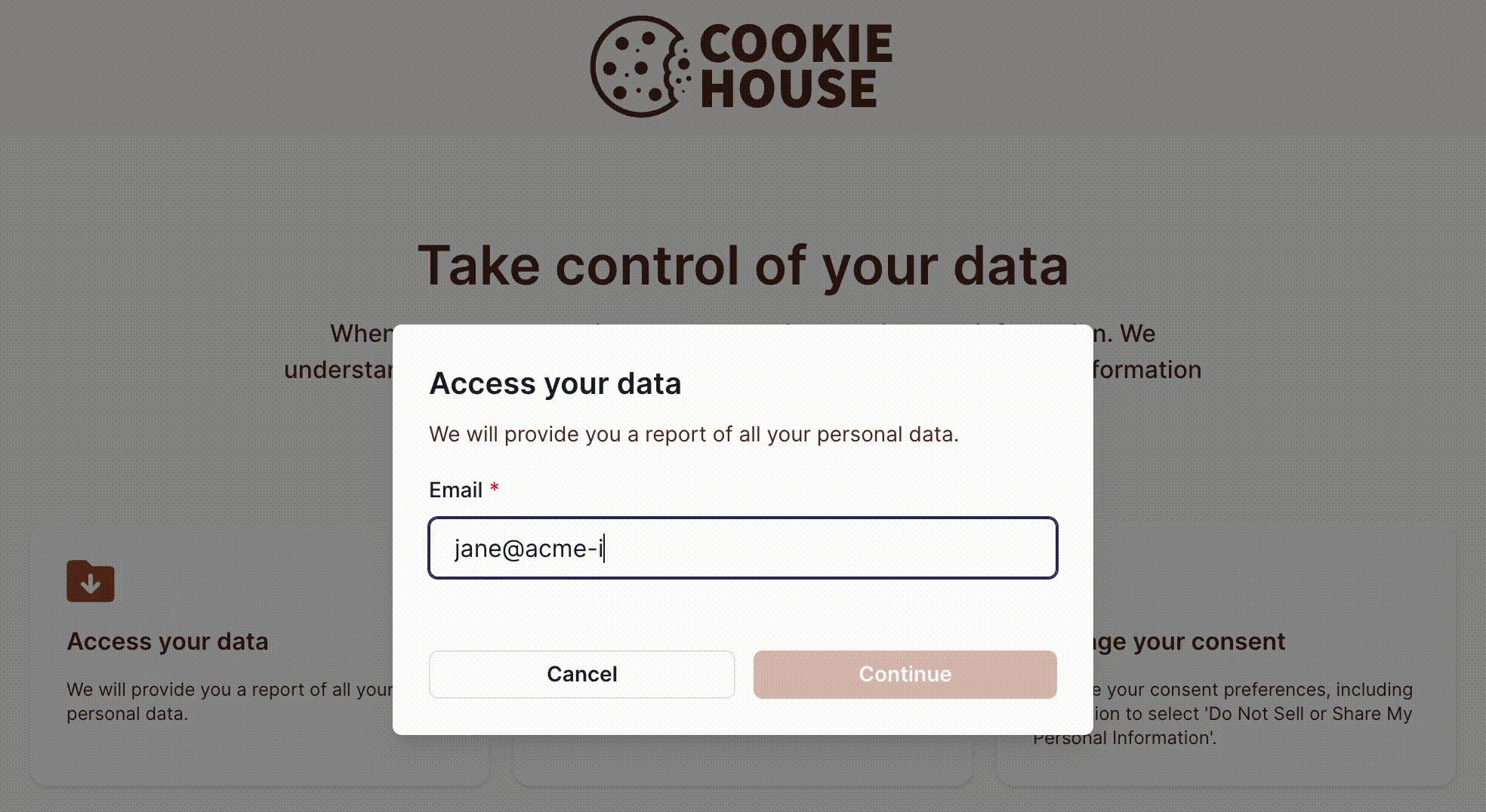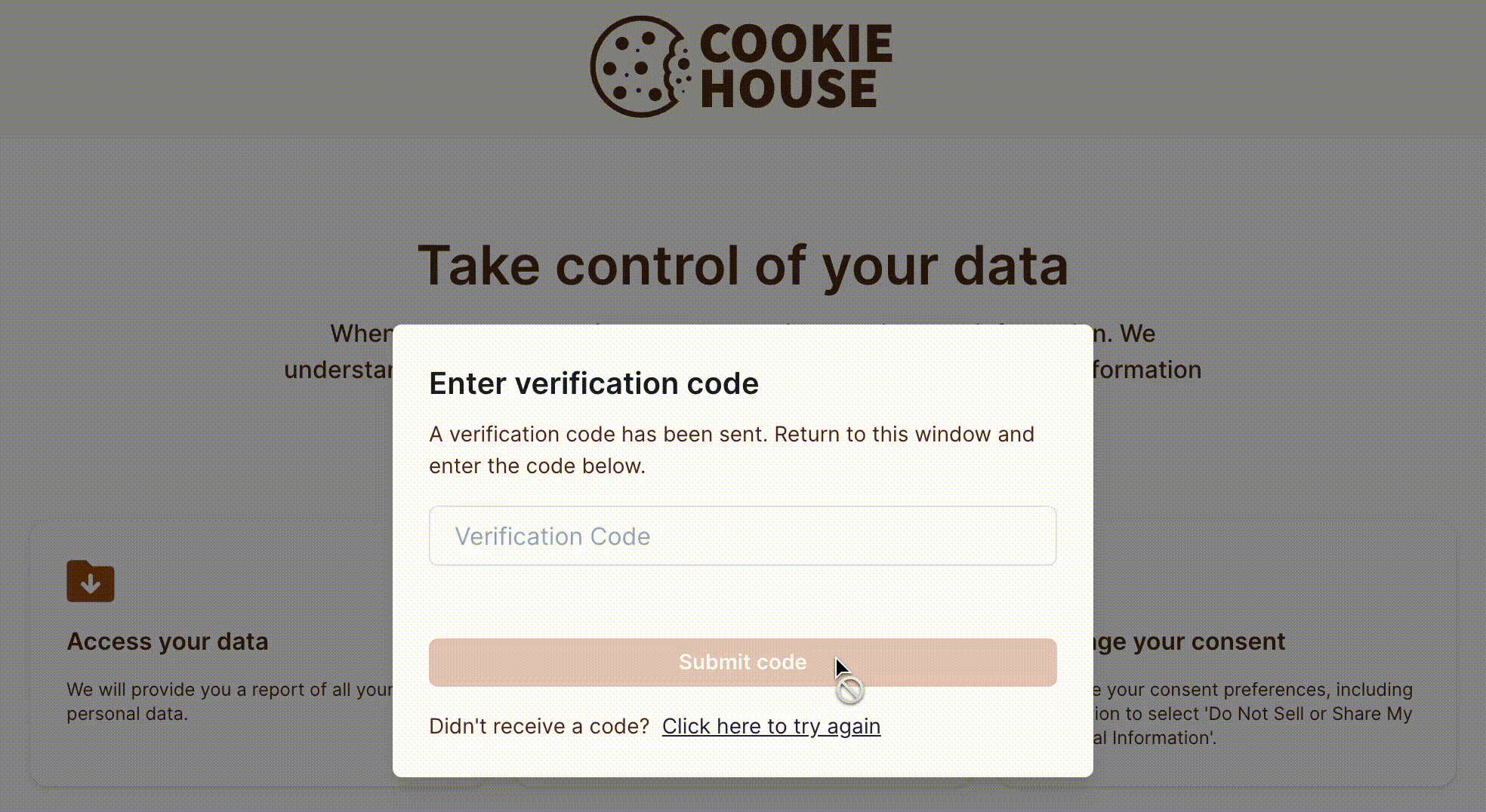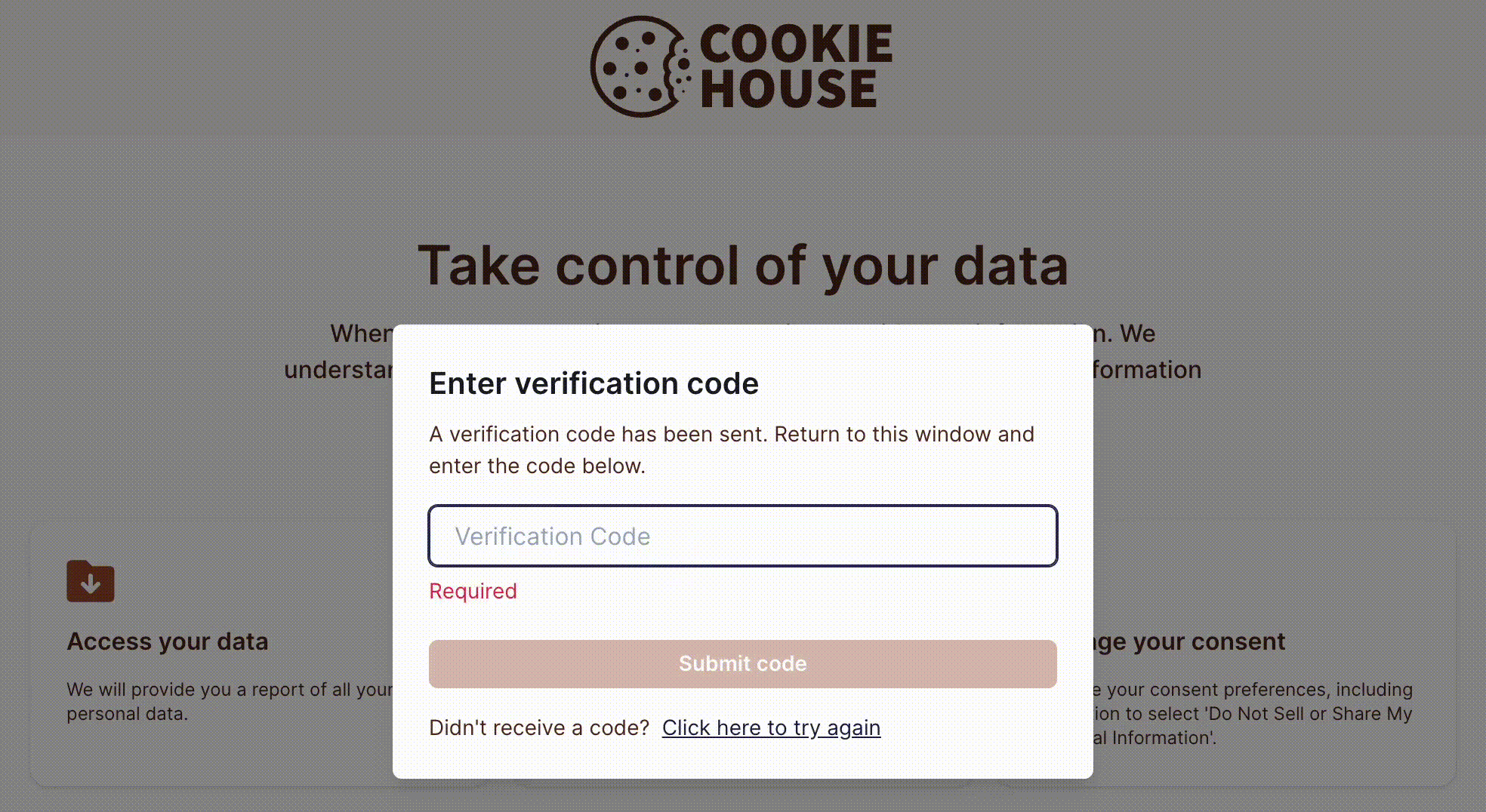
To submit a privacy request, the subject must provide an identifier, such as their email address or phone number, as shown in the example below:
Customizing the Privacy Center
The Privacy Center's appearance is highly configurable and these guides will show you how to customize the appearance to match your brand:
To configure which privacy request functions appear in your Privacy Center, please follow our guide for Configuring privacy request functions.